Advanced cyber
threat intelligence
Improve your security architecture to protect your business against advanced threats and malware.

Threat Landscape Overview
Holistic approach to threat intelligence.
Seamless Data Exchange
Secure sharing and interoperability at its core
AI-Driven Analysis
Automate and expedite operational tasks within the threat intelligence lifecycle
Threat Landscape Overview
Holistic approach to threat intelligence.
Seamless Data Exchange
Secure sharing and interoperability at its core
AI-Driven Analysis
Automate and expedite operational tasks within the threat intelligence lifecycle
Threat Landscape Overview
Holistic approach to threat intelligence.
Seamless Data Exchange
Secure sharing and interoperability at its core
AI-Driven Analysis
Automate and expedite operational tasks within the threat intelligence lifecycle
Threat detection
Enhanced threat detection and real-time monitoring
Our threat intelligence platform has hunts capabilities to integrate with organization's IDS. Real-time monitoring and smart alerts ensure safety and security of your premises.
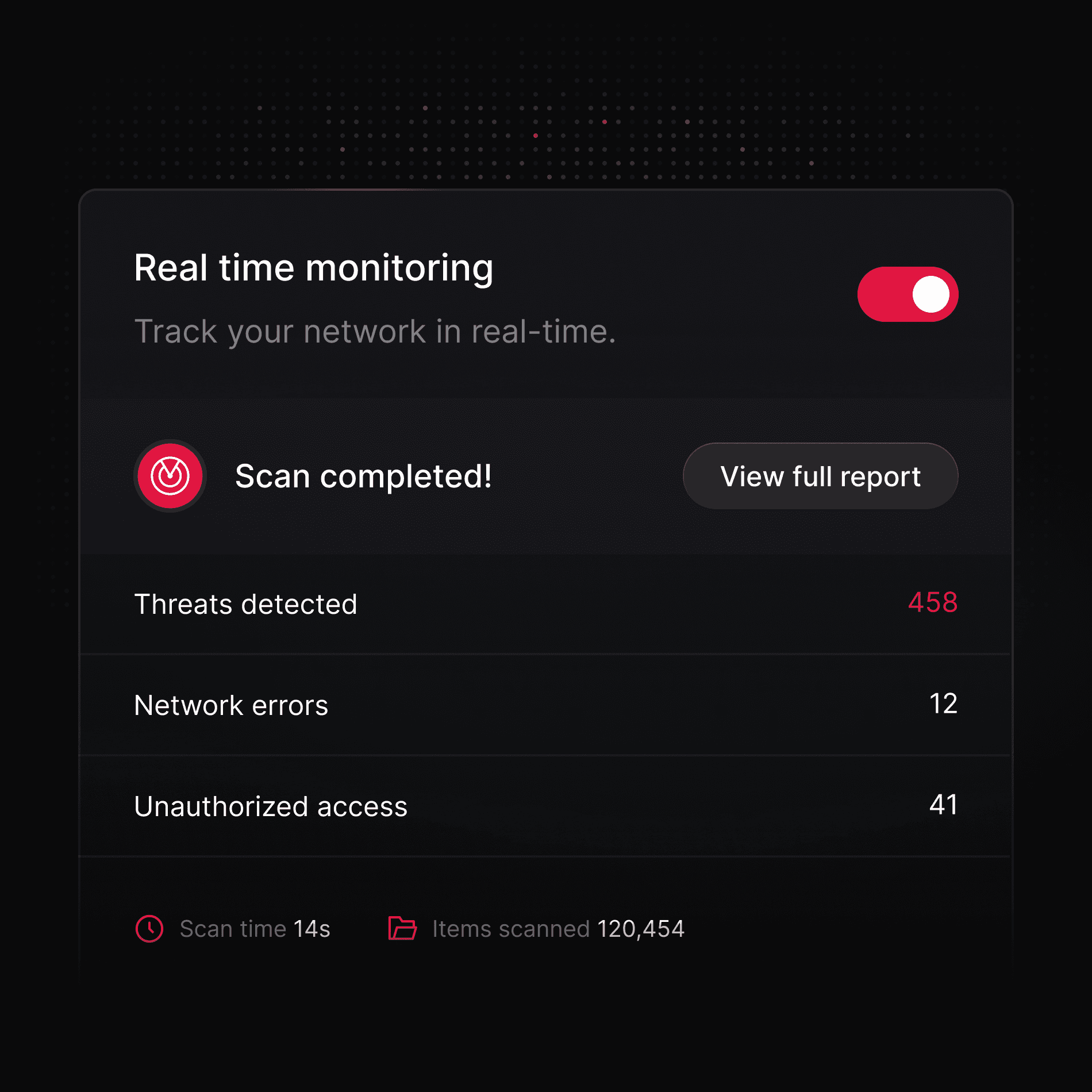
Threat detection
Enhanced threat detection and real-time monitoring
Our threat intelligence platform has hunts capabilities to integrate with organization's IDS. Real-time monitoring and smart alerts ensure safety and security of your premises.

Threat detection
Enhanced threat detection and real-time monitoring
Our threat intelligence platform has hunts capabilities to integrate with organization's IDS. Real-time monitoring and smart alerts ensure safety and security of your premises.

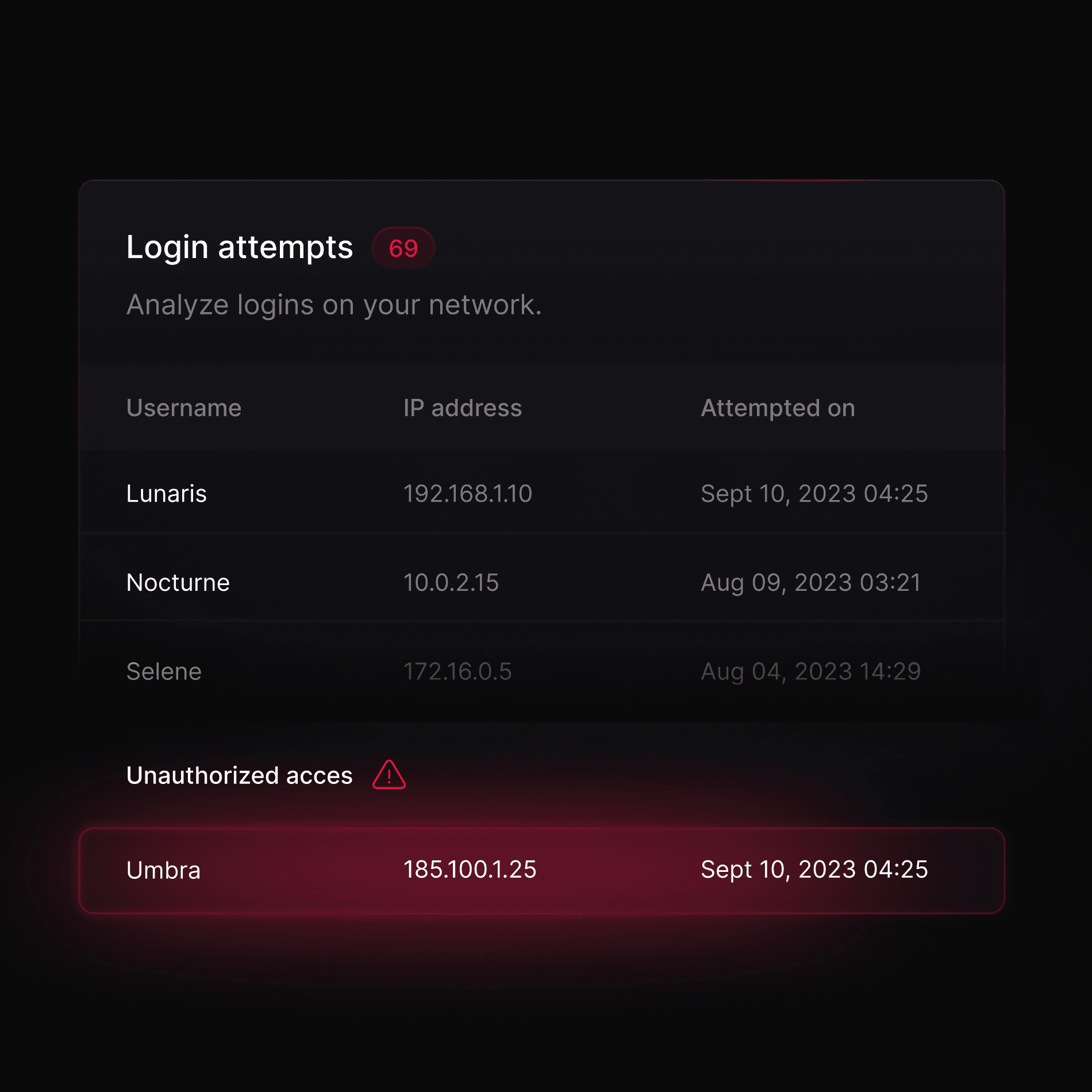
Secure access
Automated collection of security events
Our system offers an automated capability to collect security events from internal systems and integrate seeamsly with threat intelligence capabilities.

Secure access
Automated collection of security events
Our system offers an automated capability to collect security events from internal systems and integrate seeamsly with threat intelligence capabilities.

Secure access
Automated collection of security events
Our system offers an automated capability to collect security events from internal systems and integrate seeamsly with threat intelligence capabilities.
Scale with security
Are you ready to take your organization's security to the next level?
Stay ahead of threats
Customized pricing options
Scale with security
Are you ready to take your organization's security to the next level?
Stay ahead of threats
Customized pricing options
Scale with security
Are you ready to take your organization's security to the next level?
Stay ahead of threats
Customized pricing options
BLACKROUTE
Your trusted partner for cyber threat intelligence.
© 2024 BLACKROUTE. All rights reserved.
BLACKROUTE
Your trusted partner for cyber threat intelligence.
© 2024 BLACKROUTE. All rights reserved.
BLACKROUTE
Your trusted partner for cyber threat intelligence.
© 2024 BLACKROUTE. All rights reserved.